Introduction to token network
General token network command card ring network (TokenRing) and token bus network (TokenBus). TokenBus based on the IEEE802.4 standard is a physical bus structure, and its sites form a logical ring structure, and the token runs on the logical ring, and its operating principle is basically the same as that of TokenRing. TokenBus is rarely used; TokenRing is a network structure based on the IEEE802.5 standard. Most of the token ring network refers to the realization of IBM's token passing ring network, which has two transmission rates of 4Mb/s and 16Mb/s. The main feature of the token ring network transmission is that it can ensure that each node device can obtain access to the network at a predetermined time interval, which is suitable for applications with high real-time requirements. Due to the high price of this kind of network equipment, it is not conducive to popularization. In addition, it lacks support for multiple services and QoS, and there are few examples of domestic applications.
The basic principle of the token ring network is to use tokens (representing signalling permissions) to avoid conflicts in the network. Compared with the Ethernet that uses the conflict detection algorithm CSMA/CD, it improves the data of the network. Transmission rate. In addition, you can also set the priority of sending. The data transfer rate of a 4M token ring network is equivalent to that of a 10M Ethernet, and the data transfer rate of a 16M token ring network is close to a 100M Ethernet. However, the network cannot be reused, resulting in low network utilization. When a node in the network gets the token to use the network, no matter how much bandwidth the node uses, other nodes must wait for it to use up the network and give up the token before they have the opportunity to apply for the token and use the network. In addition, special nodes are required to maintain tokens in the network.
Token Ring also implies that in addition to the use of tokens, this is also a ring network topology. Token Ring is the second layer (data link layer) protocol in the OSI 7-layer model. In addition to 4Mbps and 16Mbps, IEEE 802.5 also defines data rates of 100Mbps and 1Gbps, but the latter two are rarely used.
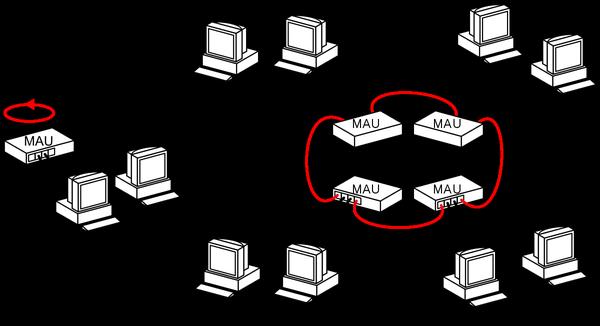
The token ring network was developed by IBM in the mid-1980s. It has been IBM's network standard for a long time and is supported by all IBM computers. Token Ring can connect to other networks with bridges or routers. The token ring network is indeed a "ring" network in practical applications, but because of the use of so-called multi-station access unit equipment, star-shaped wiring can be realized. Such a device has a certain degree of intelligence and will loop up unused ports to make the token smooth. The IEEE 802.5 standard is mainly based on IBM's token ring network, but there are some subtle differences.
The working status of the token network
The token network is like a local area network composed of three ABC computers. If ABC wants to send data packets out at the same time, there will be conflicts. So it must A token is required. Which machine obtains the token can send out the message. Then the token can be sent to that machine to send out the message. The token has two states of "idle" and "busy" in the work. "Idle" means that the token is not occupied, that is, there is no computer in the network transmitting information; "Busy" means that the token is occupied, that is, there is information being transmitted in the network. The computer that wishes to transmit data must first detect the "idle" token, set it to the "busy" state, and then transmit data behind the token. When the transmitted data is received by the destination node computer, the data is removed from the network and the token is reset to "idle". The disadvantage of the token ring network is that it needs to maintain the token. Once the token is lost, it will not work. It is necessary to select a dedicated node to monitor and manage the token. Due to the rapid development of Ethernet technology, the token network has inherent shortcomings. Tokens are no longer common in the entire computer local area network. Most of the original manufacturers of token network equipment have also withdrawn from the market. Therefore, token networks can be said to be in the local area network market. "Yesterday's Yellow Flower".
TokenRing was launched by IBM in 1969 and was later listed as the IEEE802.5 standard protocol. It is physically and logically based on the ring structure, and the transmission rate can reach 4 or 16 Mbps. The token ring network uses twisted pair or coaxial cable as the transmission medium, and connects the interfaces connected to each station one by one to form a closed loop. Each ring interface on the ring has two working modes: sending mode And the transfer method.
The network uses a small free token (FreeToken, a special signal frame different from the data signal frame) to control and manage the use of transmission media in a one-way loop on the ring to ensure There is only one station in the sending mode at most in the entire loop, and all other stations are in the receiving mode. In the receiving and forwarding mode, the corresponding station and the ring interface are actually disconnected. At this time, the ring interface first receives one bit each time and copies it to the buffer area. After inspection or modification (only one bit delay is caused), Forward it again. At this time it monitors two special bit combinations: the address of the site and the free token.
When the ring interface corresponding to the station that wants to send data detects the free token, the free token is changed to a busy token (data signal frame), and the station is connected at the same time, and the sending mode is entered. Send the data in the buffer area by the ring interface bit by bit, and then disconnect the station after the transmission is completed, and return to the receiving and transferring mode. When the ring interface in the receiving and forwarding mode detects the data signal frame with the address of the station, it connects to the station, and while continuing to forward the bit stream, it is copied to the connected station bit by bit, and on the data frame After the data signal frame has been received, the station will be disconnected. Then when the data frame returns to the sending station, it will be absorbed by it and a free token will be inserted.
The media access control mechanism of the brand ring network adopts the circular method of distributed control mode. In the token ring network, a token (Token) is passed along the ring bus between the computers of the network access nodes. The token is actually a frame with a special format, which does not contain information. It only controls the use of the channel to ensure that the Only one node can monopolize the channel at the same time. When all nodes on the ring are idle, the token travels around the ring. The node computer can only send the data frame after obtaining the token, so there is no collision. Since the tokens are delivered in sequence on the network ring, access rights are fair to all computers on the network.
In this kind of network, there is a special frame called "token", which is continuously transmitted on the loop to determine when a node can send a packet. The token is 24 bits long and has three 8-bit fields, which are the first delimiter (StartDelimiter, SD), access control (AccessControl, AC), and the final delimiter (EndDelimiter, ED). The first delimiter is a distinctive signal pattern, which is manifested as a non-data signal, and its purpose is to prevent it from being interpreted as other things. This unique 8-bit combination can only be recognized as the start of frame identifier (SOF).
Transmission method
When sending data, the computer that holds the token will send the data first. The computer receiving the data will check the frame header, and process it if it is sent to itself. Regardless of whether it is given to yourself, it will be passed on again. After a round of transmission, check whether the data is the same to make sure that the data has no transmission errors. After sending the data, you can adjust the priority of the token as needed (change it to be lower than your own priority), and then pass the token to the next computer. If the token is received but the priority is higher than its own, the token must be passed to the next computer.
Token Ring Network
Token Ring Network (TokenRing) is a LAN protocol defined in IEEE802.5, in which all workstations are connected to a ring, each A workstation can only transmit data with directly adjacent workstations. The transmission authority is granted to the workstation through the token information surrounding the ring.
The small data (frame) transmitted on the token ring is called a token, and whoever has the token has the transmission authority. If a station on the ring receives the token and has information to send, it changes one bit in the token (this operation turns the token into a frame start sequence), adds the information it wants to transmit, and then sends the entire information Go to the next station in the ring. When this information frame is transmitted on the ring, there is no token in the network, which means that other workstations must wait to transmit data. Therefore, there is no transmission conflict in the token ring network.
The information frame is transmitted along the ring until it reaches the destination, and the destination creates a copy for further processing. The information frame continues to travel along the ring until it reaches the sending station and can be deleted. The sending station can check the return frame to see if the frame is received and copied by the receiving station.
Token network protocol structure
123915bytes
SDELACFCDestinationAddressSourceAddress
Routeinformation0-30bytes
Information(LLCorMAC) variable
FCS(4bytes)EDELFS
SDEL/EDEL―Starting Delimiter/EndingDelimiter (StartingDelimiter/EndingDelimiter).
AC-Access Control (AccessControl) field includes priority field.
FC-Frame Control (FrameControl) field indicates whether the frame contains data information or control information.
DestinationAddress-DestinationStationAddress.
SourceAddress——SourceStationAddress (SourceStationAddress).
RouteInformation-This field includes routing control, routing descriptor and routing type information, etc.
Information-Information (Information) field may be LLC or MAC.
FCS-Frame Check Sequence (FrameCheckSequence)
FrameStatus-Start from the frame receiver, identify the signal address, and whether the frame copy is successful.
