The second layer switch
Concept
As we all know, the second layer switch is based on the MAC address of the second data link layer and selects the route through the station table To complete the end-to-end data exchange.
Work flow
The specific work flow of the Layer 2 switch is as follows:
(1) When the switch receives a data packet from a certain port, it reads first Take the source MAC address in the frame header, and store the corresponding MAC address and source port in the station table.
(2) Then read the destination MAC address in the frame header, and look up the corresponding port in the address table;
(3) If there is a destination MAC address in the table The port corresponding to the address, the data packet is directly copied to this port;
(4) If the corresponding port is not found in the table, the data packet will be broadcast to all ports under the same VLAN, as the destination machine When responding to the source machine, the switch can learn which port a destination MAC address corresponds to, and it is no longer necessary to broadcast to all ports the next time it transmits data.
Continuously looping this process, the MAC address information of the entire network can be learned. This is how the Layer 2 switch establishes and maintains its own address table.
Because the establishment and maintenance of the station table is automatically completed by the switch, and the router belongs to the third layer of equipment, its addressing process is based on IP address addressing and generated through routing tables and routing protocols. Therefore, the biggest advantage of the second layer switch is the fast data transmission speed, because it only needs to identify the MAC address in the data frame, and the algorithm for selecting the forwarding port directly based on the MAC address is very simple, which is very easy to implement with ASIC dedicated chips. Obviously, the solution of the second layer switch is actually a cheap solution of "switching everywhere". Although this solution can also divide subnets, restrict broadcasting, and establish VLANs, its control ability is small, and flexibility is not enough. Unable to control the flow of each information point, lack of convenient and practical routing function.
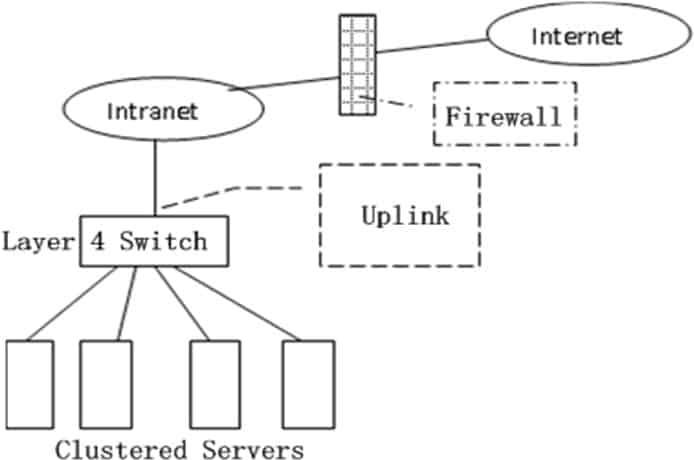
The third layer switch
Concept
The third layer switch completes the end-to-end data exchange directly based on the third-layer network layer IP address.
Working principle
The working principle of the three-layer switch:
Device A using IP--------------- ---------Layer 3 switch ------------------------ Device B using IP
For example, A To send data to B, knowing the destination IP, then A uses the subnet mask to obtain the network address to determine whether the destination IP is in the same network segment as itself.
If you are on the same network segment, but don’t know the MAC address required to forward the data, A will send an ARP request, B will return its MAC address, and A will encapsulate the data packet with this MAC and send it to the switch, the switch Activate the two-layer switching module, look up the MAC address table, and forward the data packet to the corresponding port.
If the destination IP address is not in the same network segment, then A needs to communicate with B. If there is no corresponding MAC address entry in the flow cache entry, the first normal data packet will be sent to a fault. Provincial gateway, this default gateway is generally set in the operating system, corresponding to the third layer routing module, so it can be seen that for data that is not in the same subnet, the MAC address of the default gateway is first placed in the MAC table; then The three-layer module receives this data packet and queries the routing table to determine the route to B. A new frame header will be constructed, with the MAC address of the default gateway as the source MAC address and the MAC address of host B as the destination. MAC address. Through a certain recognition trigger mechanism, the correspondence relationship between the MAC addresses and forwarding ports of host A and B is established, and recorded into the flow cache entry table. The subsequent data from A to B is directly handed over to the layer 2 switching module for completion. This is usually referred to as one route and multiple forwarding.
On the surface, the third layer switch is a combination of the second layer switch and the router. However, this combination is not a simple physical combination, but a logical combination of each based on their strengths. Its important performance is that when the first data flow of a certain information source is exchanged at the third layer, the routing system will generate a MAC address and IP address mapping table, and store the table, when the same information When the subsequent data flow of the source enters the switching environment again, the switch will directly transmit from the source address to the destination address from the second layer according to the address mapping table generated and saved for the first time, without being processed by the third routing system, thereby eliminating The network delay caused by route selection improves the forwarding efficiency of data packets and solves the rate bottleneck caused by routing when information is transmitted between networks. Therefore, the third layer switch can not only complete the port switching function of the second layer switch, but also complete the routing function of some routers. That is, the switch solution of the third layer switch is actually a solution that can support multi-level dynamic integration. Although this multi-level dynamic integration function can also be carried out by traditional routers and second-level switches to some extent, but Compared with the adoption of a three-layer switch, this kind of carrying solution not only requires more equipment configuration, takes up more space, designs more wiring and costs higher costs, but also has much worse data transmission performance because of the In mass data transmission, the router in the carrying solution cannot overcome the bottleneck of routing transmission rate.
The fourth layer switch
Introduction
Obviously, the second layer switch and the third layer switch are the end-to-end switching process based on the port address, although This MAC address and IP address-based switch technology can greatly improve the data transmission rate between nodes, but it cannot determine or dynamically limit the switching process and data flow of the port according to the application requirements of the port host. The fourth layer of intelligent application exchange requirements. The fourth layer switch can not only complete end-to-end switching, but also determine or limit its switching traffic according to the application characteristics of the port host. Simply put, the fourth layer switch is based on the exchange process of the transport layer data packet, and is a new type of LAN switch based on the user application exchange requirements of the TCP/IP protocol application layer. The fourth layer switch supports all protocols below the fourth layer of TCP/UDP, and can identify at least 80 bytes of data packet header length, and can distinguish the application type of the data packet according to the TCP/UDP port number, thereby achieving application layer access Control and service quality assurance. Therefore, the fourth layer switch is not so much a hardware network device as it is a software network management system. In other words, the fourth layer switch is a type of network management switching equipment that is based on software technology and supplemented by hardware technology.
Finally, it’s worth pointing out that some people still have some vague concepts to varying degrees. They think that the so-called fourth-tier switch actually adds the ability to distinguish the fourth-tier protocol on the third-tier switch. The port capability only adds some value-added software to the third layer switch. Therefore, it does not work at the transport layer, but still performs switching operations on the third layer. It is just more sensitive to the third layer exchange. Fundamentally deny the key technology and role of the fourth layer of exchange. We know that the second layer IEEE802.1P field or the third layer IPToS field of the data packet can be used to distinguish the priority of the data packet itself. We say that the fourth layer switch is based on the fourth layer data packet exchange, which means that it can be based on The fourth layer TCP/UDP port number is used to analyze the data packet application type, that is, the fourth layer switch not only has all the switching functions and performance of the third layer switch, but also supports the network traffic and service quality that the third layer switch cannot have Intelligent control function.
Important technology
As mentioned above, the second layer of switching equipment relies on the MAC address and the VLAN tag information of the 802.1Q protocol to complete the link layer switching process, the third layer The switching/routing equipment uses the IP address information for network path selection to complete the switching process, and the fourth layer switching equipment uses the header information of the transport layer data packet to help information exchange and transmission processing. That is to say, the specific content described by the exchange information of the fourth layer switch is essentially all the protocols or processes contained in each IP packet, such as HTTP for Web transmission, FTP for file transmission, and Telnet for terminal communication, SSL and other protocols for secure communication. In this way, in an IP network, the commonly used fourth layer exchange protocol is actually TCP (used for connection-based dialogue, such as FTP) and UDP (used for connection-based communication, such as SNMP or SMTP). .
Because the header of TCP and UDP packets not only includes the "port number" field, it also indicates what type of network data the packet is being transmitted, and uses this information related to specific applications (Port number), you can complete a large number of quality services related to network data and information transmission and exchange. The most noteworthy of these are the following five important application technologies, because they are the main technologies commonly used in the fourth layer of switches.
Packet filtering/security control
On most routers, using the fourth layer of information to define filtering rules has become the default standard, so many routers are used as packet filtering firewalls. On this kind of firewall, not only can you configure to allow or prohibit connections between IP subnets, but you can also control the communication of designated TCP/UDP ports. Unlike traditional software-based routers, the main difference between layer 4 switching and layer 3 switching is that this filtering capability is implemented in a high-speed chip dedicated to ASIC, which enables this security filtering control mechanism It can be carried out at full wire speed, which greatly improves the packet filtering rate.
Quality of Service
In the hierarchical structure of the network system, the fourth layer of TCP/UDP information is often used to establish application-level communication priority permissions. If there is no concept of layer 4 switching, the quality of service/level of service will inevitably be subject to the information provided by the second and third layers, such as MAC addresses, switching ports, IP subnets or VLANs. Obviously, in the information communication, when the lack of fourth-level information is hindered, the priority of emergency applications cannot be discussed, which will greatly prevent the rapid transmission of emergency applications on the network. The fourth layer switch allows to distinguish the priority based on the combination of the destination address and the destination port number (application service), so that emergency applications can obtain high-level services of the network.
Server Load Balancing
The fourth layer of information is crucial when providing support for balancing traffic load among multiple servers with similar service content. Therefore, the fourth layer switch in the core network system, responsible for load balancing between servers is a very important application. The server load balancing method supported by the fourth layer switch is to combine the IP addresses with load balancing services to form a set through different physical servers to provide the same service together and define it as a single virtual server. This virtual server is a logical server with a separate IP address. User data streams only need to point to the IP address of the virtual server, instead of directly communicating with the real IP address of the physical server. Only after the network address translation (NAT) performed by the switch, the server that has not registered an IP address can obtain the ability to be accessed. Another advantage of this definition of a virtual server is that after the actual IP address of the server is hidden, unauthorized access can be effectively prevented.
The virtual server is defined based on the application service (the fourth layer TCP/UDP port number), so that the independent server can be a member of the virtual server. Using the fourth-level dialogue flag information, the fourth-level switch can use many load balancing methods to convert communication traffic in the virtual server group. Among them, OSPF, RIP, and VRRP protocols are consistent with wire-speed switching and load balancing. The fourth layer switch can also use the complex mechanism provided by the TRL (TransactionRateLimiting) function to contain or deny services of different application types according to traffic characteristics. You can use the CRL (ConnectionsRate Limiting) function to enable the network administrator to specify the number of connections allowed in a given time to ensure QoS. Or, with the SYN-Guard function, to ensure that those legitimate connections that meet the TCP protocol can query network services.
Host backup connection
Host backup connection provides redundant connections for port devices, thereby effectively protecting the system in the event of a switch failure. This service allows the definition of master and backup switches, similar to virtual The server definitions are the same, and they have the same configuration parameters. Since the fourth layer switches share the same MAC address, the backup switch receives all the same data as the main unit. This enables the backup switch to monitor the communication content of the main switch service. The main switch continuously informs the backup switch of the relevant data of the fourth layer, MAC data and its power supply status. When the main switch fails, the backup switch will automatically take over without interrupting the conversation or connection.
Statistics
By querying the fourth layer data packet, the fourth layer switch can provide more detailed statistics records. Because the administrator can collect more detailed information about which IP address is communicating, and even collect communication information according to which application layer service is involved in the communication. When the server supports multiple services, these statistics are especially effective for examining the load of each application on the server. The added statistics service is also very useful for server load balancing service connections that use switches.
