DefinitionofTrafficShaping
TrafficShapingisameasuretoactivelyadjusttherateoftrafficoutput.
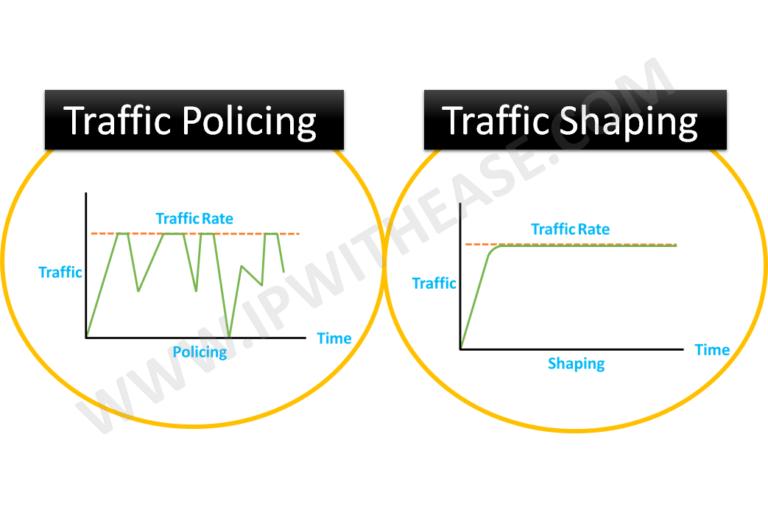
AtypicalapplicationistocontroltheoutputoflocaltrafficbasedontheTPindexofthedownstreamnetworknode.Themaindifferencebetweentrafficshapingandtrafficpolicingisthattrafficshapingbuffersthepacketsthatneedtobediscardedintrafficpolicing—usuallyputtingtheminabufferorqueue,alsoknownasTrafficShaping(TS).Whenthereareenoughtokensinthetokenbucket,thesecachedmessagesaresentoutevenly.Anotherdifferencebetweentrafficshapingandtrafficpolicingisthatshapingmayincreasedelay,whilepolicinghardlyintroducesadditionaldelay.
Asshowninthefigureabove,whenamessagearrivesattheinterface,themessageisfirstclassifiedandprocessedaccordingtothefollowingsituations.
Forpacketsthatdonotparticipateintrafficshaping,continuetosenddirectly.
Forpacketsparticipatingintrafficshaping,ifthereisashapingqueue,thepacketsenterthequeuedirectly,andthewaitingqueuewillscheduleandforwardthepacketsaccordingtotheshapingalgorithm.
Forpacketsparticipatingintrafficshaping,ifthereisnoshapingqueue,theshapingalgorithmdetermineswhetherthepacketissent.
Whenamessagearrivesattheinterfaceandtheshapingqueueisfull,themessageisdiscarded.
Thecorealgorithmoftrafficshaping
Therearetwocorealgorithmsoftrafficshaping.ThespecifictechnologyusedisGTS(GenericTrafficShaping),generaltrafficshaping:
LeakyBucketAlgorithm
LeakyBucket
LeakyBucketalgorithmisoftenusedinthenetworkworldintrafficshaping(TrafficShaping)orratelimiting(RateLimiting)Analgorithmwhosemainpurposeistocontroltherateofdatainjectionintothenetworkandsmooththebursttrafficonthenetwork.Theleakybucketalgorithmprovidesamechanismthroughwhichbursttrafficcanbeshapedtoprovideastableflowforthenetwork.
TokenBucketAlgorithm
TokenBucket
Sometimespeoplemistakenlyconfusetheleakybucketalgorithmwiththetokenbucketalgorithm.Infact,thesetwoalgorithmshavecompletelydifferentcharacteristicsandareusedforcompletelydifferentpurposes.Themaindifferencebetweenthemisthattheleakybucketalgorithmcanforciblylimitthedatatransmissionrate,whilethetokenbucketalgorithmcanlimittheaveragedatatransmissionratewhilealsoallowingacertaindegreeofbursttransmission.
Insomecases,theleakybucketalgorithmcannoteffectivelyusenetworkresources.Becausetheleakagerateoftheleakybucketisafixedparameter,evenifthereisnoresourceconflictinthenetwork(nocongestionoccurs),theleakybucketalgorithmcannotmakeasingleflowbursttotheportrate.Therefore,theleakybucketalgorithmisinefficientfortrafficwithburstcharacteristics.Thetokenbucketalgorithmcansatisfytheseburstytraffic.Generally,leakybucketalgorithmandtokenbucketalgorithmcanbecombinedtoprovidegreatercontrolovernetworktraffic.
Commontrafficshapingclassification
GTSgeneraltrafficshaping
Trafficshapingforcesthetraffictofollowacertainbandwidthallocationlimitbyreducingtherateofoutgoingtraffic.Unliketrafficpolicing,whichdiscardsthetrafficthatexceedstheburstsize,itputstheburstoftrafficintothetrafficshapingbuffer,andthensendsitoutwhenthebandwidthisavailable,orthenumberofbuffereddatapackets.Whenitislowerthantheconfiguredlimit,itwillbesentoutagain.
Trafficshapingusesatokenbucketsystemtodeterminewhethertotransmit,delayordiscardnewpackets.Usingthistokenbucketsystem,eachinterfacehasacommittedinformationrate(CIR),whichistherateatwhichtheinterfacecantransmitdatapacketsinaperiodoftime.Thecontinuousburstrate(Bc)definesthemaximumnumberoftokensthatthetokenbucketcancontaininanothertimeinterval.Whenadatapacketarrivesataninterface,itwilltakeoutatokenfromthetokenbucket.Whenthedatapacketissent,thetokenwillbereleased.Whenthetimeinterval(Tc)haspassed,thetokenwillbereturnedtothetokenbucket.Ifthetokenbucketisempty,anynewpacketsarrivingatthatinterfacewillbeputinthequeueuntilthetimeintervalhaspassedandthetokenwillberefilled.IftheCIRcontinuestoexceed,tokenswillberemovedfromthetokenbucketatarategreaterthantheywereaddedtofillthequeueandcausepacketstobediscarded.
TrafficshapingcanbeappliedtoanumberofdifferentLayer2technologies,suchasEthernet,ATM,HDLC,PPP(ISDNanddial-upinterfacesarenotsupported),andframerelay.Withtheexceptionofframerelay,allofthesetechnologiessupportGeneralTrafficShaping(GTS).GTScanalsoshapeacertaintypeoftrafficdefinedintheaccesscontrollistbyspecifyingagroupinthetrafficshaping.
InordertoconfiguretheGTS,youmustknowthetargetbitratefortheinterface,thatis,thecommittedinformationrate(CIR),whichreferstotherateatwhichtrafficissentundernormalconditions.Continuousburstrate(Bc)referstotherateatwhichtrafficisallowedtoburstbeyondthenormaltrafficrateineachtimeinterval,expressedinbits.Excessiveburstrate(Be)referstotherateatwhichtrafficisallowedtoburstbeyondthesustainedburstrateinthefirsttimeinterval.Everytimeinterval(Tc),trafficwillbefilledintothetokenbucketoftrafficshaping.
Tc=Bc/CIR
Thetimeintervaloftrafficshapingcannotbelessthan10msorgreaterthan125ms.TherouterfindsthebesttimeintervalbasedontheformulaTc=Bc/CIR.Thedefaulttimeintervalis125ms.ThistimeintervalistheresultofCIRandBcconfigurationandisusedfornon-configurability.CiscorecommendsthatBcshouldbe1/8ofCIR.Itwillgenerate8intervalsof125mspersecond.
ConfigureGTSforallinterfacetraffic,andusethetraffic-shapingratecommandontheinterfacethatneedstrafficshaping.Forspecifictraffic,usethetraffic-shapinggroupcommandandanaccesscontrollist.
traffic-shaping{rate|groupaccess-list-number}target-bit-rate[sustained][excess][buffer-limit]
groupaccess-list-numberspecifiedAlltrafficmatchingtheaccesscontrollist(1-2699)isshaped.
ratespecifiesthatalltrafficonthisinterfacewillbeshaped.
target-bit-rateThenormalrate(CIR)atwhichthetrafficwillbetransmitted,rangingfrom8000tothecompleteCIRexpressedinbitspersecondoftheinterface.
sustainedsustainedbitrate(Bc)referstothevalueoftrafficallowedtoburst,expressedinbitsineachtimeinterval.
ExcessExcessivebitrate(Be)referstotheburstoftrafficexceedingthecontinuousbitrateinthefirsttimeinterval,expressedinbitsineachtimeinterval.Itisanoptionalparameter,itwillassumethatthetokenbucketiscompletelyfull:Be=Bc*2.
bufferisusedtospecifyabufferlimit,rangingfrom1to4096.
GTSconfigurationrequirestwosteps:discoverthevalueoftrafficshaping,andconfiguretrafficshapingontheinterface.
1.Findthecorrectvaluefortrafficshaping.CIR,Bc,Be
Bcspecifiesthenumberofbitsthattheinterfacecantransmitinacertaintimeinterval.Bc=CIR*Tc
Bespecifiesthebursttrafficthatcanbesupportedwhentheinterfaceisfilledwithenoughtokens,usuallyinthefirsttimeinterval.Be=Bc*2
Iftheinterfacedoesnotsupportburst,youcanusethefollowingformula:Be=Bc
2,intheinterfacemode,usethetraffic-shapingcommandtoenabletrafficshaping.
ToviewtheGTSconfiguration,usetheshowtraffic-shaping[statistics]command
FrameRelayTrafficShaping(FRTS)
Underthefollowing4situationsWhenusingFRTS:1centerhighspeedandlowbranchspeed.2AsinglephysicallinecarriesmanyVCstodifferentdestinations.3IfcongestionoccursinFR,Iwanttheroutertoblockthedataflow(Throttle).4Itisnecessarytotransmitdatastreamsofmultipleprotocols(IP,SNA)onthesameFRVC,andhopethateachdatastreamcanaccountforacertainamountofBW.
TheFECNandBECNinFRareusedtoimplythatcongestionoccursonthenetwork.WhenadatapacketwithaBECNmarkisreceived,FRTrafficShaping(FRTS)willdynamicallyshapethetraffic.Note:FRTScanonlybeusedonFRPVCandSVC.AmongthemisanadaptiveFRTS.IneachTcinterval,theprocesswillcheckwhetherBECNisreceivedfromtheframerelaynetwork.IfBECNisreceivedinaTcinterval,thetransmissionratewillbereducedby25%untilitdropstohalfoftheCIR.until.IfandonlyifBECNisnotreceivedwithin16Tc,thecommunicationrateisrestoredtoCIR.
FRTSconfigurationsteps
1)CreateaMAP-CLASS,thenameiscasesensitive.
2)Definethemethodoftrafficshaping,suchassettingtheaveragerateandthemaximumrate.
3)EncapsulateFRAME-RELAYontheinterface.
4)ApplyMAP-CLASS5totheportandenabletrafficshaping,whichisgenerallyusedforthesourceinterface.
Trafficsupervision
RouterAsendspacketstoRouterB.Inordertoreduceunnecessarylossofpackets,thepacketscanbetraffic-shapedattheexitofRouterA.CachethepacketsthatexceedthetrafficshapingfeatureinRouterA.Whentheshapingalgorithmallowsthenextbatchofmessagestocontinuetobesent,themessagesaretakenoutofthebufferqueuefortransmission.Inthisway,thepacketssenttoRouterBwillallcomplywithRouterB'strafficregulations.
Themaindifferencebetweentrafficshapingandtrafficpolicingis:
Trafficshapingcachespacketsthatexceedthetrafficspecificationsintrafficpolicing.Whentheshapingalgorithmallowsmessagestobesent,thesebufferedmessagesaresentoutevenly.
Trafficshapingmayincreasedelay,andtrafficpolicinghardlyintroducesadditionaldelay.
